
Home from war, veterans' trauma still ripples through families
Millions of kids are stepping up to help wounded warriors and their families deal with the impact of service.
Watch CBS News

Millions of kids are stepping up to help wounded warriors and their families deal with the impact of service.

In Michigan, Wisconsin and Pennsylvania, both Biden and Trump elicit feelings of worry, anger and nostalgia, according to latest CBS News poll.

Military families still have health concerns two years after thousands of gallons of jet fuel spilled into the Navy water supply at Hawaii's Pearl Harbor base.

It's been almost 20 years since Dan Rather signed off at the network where he spent 44 years covering wars, politics, and the assassination of JFK. But he has not retired from the life of a reporter.

South Dakota Gov. Kristi Noem addressed on social media the backlash she received after details of her soon-to-be-released book were revealed.

It's the first meeting between the two men since Florida Governor Ron DeSantis ended his 2024 presidential challenge against former President Trump.

Senate Minority Leader Mitch McConnell, in an interview with "Face the Nation," weighed in on Trump's broad immunity claims.

More than 100 tornadoes were detected in six states in the Midwest over the weekend.

Violence broke out on the UCLA campus where dueling demonstrations between pro-Israel and pro-Palestine groups got underway on Sunday, the school said.

Nvidia changed the world of video game graphics. Now CEO Jensen Huang is focused on developing technology for the age of AI.

Experts say there are rewards for not pushing yourself to the edge all the time.

Campus protesters are "looking for some sort of acknowledgement from our leadership," Democratic Rep. Summer Lee of Pennsylvania said.

Texans wide receiver Tank Dell "sustained a minor wound" in a shooting that took place early Sunday morning in Florida, the team said.

Two years after a fuel leak at the Navy's Red Hill storage complex contaminated drinking water at Pearl Harbor, the city of Honolulu is guarding against contamination to its own water supply.

A look back at 60 Minutes correspondent Scott Pelley's coverage of combat veterans overseas and the impact of post-traumatic stress disorder on their families when they return home.

Nonprofit organization World Central Kitchen is set to resume its aid work in Gaza, weeks after seven aid workers were killed.

Hanna Siegel's uncle, U.S.-Israeli citizen Keith Siegel, was one of the hostages seen in a Hamas propaganda video Saturday.

WNBA legend Candace Parker announced she's retiring after 16 years.

Prosecutors in former President Donald Trump's criminal trial in New York called two new witnesses to the stand on Friday, rounding out the first week of testimony.

The court is considering whether Trump is entitled to broad immunity from criminal charges in the 2020 election case.

There are no cameras allowed in the court where he's being tried.

"I am happy to debate him," President Biden said during an interview with Howard Stern.

Trump has in the past railed against absentee voting, declaring that "once you have mail-in ballots, you have crooked elections."

President Biden finds familiar and active allies for his reelection bid with labor union endorsements.

The hostages seen on the video were identified as Omri Miran and Keith Siegel by the campaign group the Hostages and Missing Families Forum.

Hamas says it received the cease-fire proposal from Israel after a high-level Egyptian delegation wrapped up a visit to Israel.
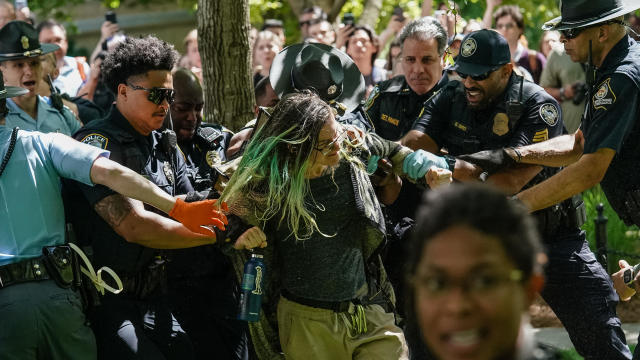
Police are cracking down at some university protests over Israel's war against Hamas in Gaza.

Laura Kowal's match on an online dating site wasn't what he seemed. Now her daughter is on a mission to expose the risk of romance scams: "It could happen to anybody."

It's been a decade since the Flint water crisis began. Residents told CBS News the scandal still weighs heavily on the city.

For more than two decades, retired Lt. Gene Eyster wondered what became of that boy he found abandoned in a cardboard box in an apartment hallway.

Gold can be a smart bet for seniors — and that's not just due to the recent gold price uptick, either.

A HELOC can be a great borrowing option now, but the repayment process is unique. Here's what to know about it.

The average American is currently facing a hefty amount of credit card debt — but there are good ways to tackle it.

Intimacy coordination is a relatively new and growing field with movie and television productions required to make a good-faith effort to hire one if needed on set.

With a relatively low average monthly cost of living and a low crime rate, this little-known town has a lot to offer retirees according to one report.

Regulators have closed Republic First Bank's 32 branches in Pennsylvania, New Jersey and New York and they will be taken over by Fulton Bank.

The income needed to join your state's top earners can vary considerably, from a low of $329,620 annually in West Virginia to $719,253 in Washington D.C.

The union struck a four-year agreement with the German company on Friday evening, just before the expiration of the previous contract.

Pick up one of these rockers from AllModern, Wayfair, Serena & Lily and more for baby's nursery.

Here's how and when to watch the Würth 400 at Dover Motor Speedway NASCAR race.

Here's how and when to watch tonight's NBA Playoffs Game 4 between the Minnesota Timberwolves and Phoenix Suns.

Thousands of gallons of jet fuel contaminated the Navy's drinking water system for Pearl Harbor. Families dealing with health issues are suing, alleging they were harmed by negligence at Red Hill.

Jensen Huang leads Nvidia – a tech company with a skyrocketing stock and the most advanced technology for artificial intelligence.

Hundreds of thousands of veterans have been diagnosed with PTSD. The children living with injured veterans are stepping up to help these wounded warriors and their families.

Two years after a fuel leak at the Navy's Red Hill storage complex contaminated drinking water at Pearl Harbor, the city of Honolulu is guarding against contamination to its own water supply.

Thousands of gallons of jet fuel contaminated the Navy's drinking water system for Pearl Harbor. Families dealing with health issues are suing, alleging they were harmed by negligence at Red Hill.

Jensen Huang leads Nvidia – a tech company with a skyrocketing stock and the most advanced technology for artificial intelligence.

Hundreds of thousands of veterans have been diagnosed with PTSD. The children living with injured veterans are stepping up to help these wounded warriors and their families.

Secretary of Commerce Gina Raimondo is focused on U.S. advanced microchip production — and keeping the chips out of China and Russia.

A piece of Holocaust history — a Nazi concentration camp built on Alderney, a British island — has been largely forgotten. Researchers are now counting the island’s dead.

She made a name for herself as an Oscar-nominated actress in "Almost Famous." But music has always been in her blood, and now Kate Hudson is making a name for herself as a singer-songwriter, with her debut album, "Glorious."
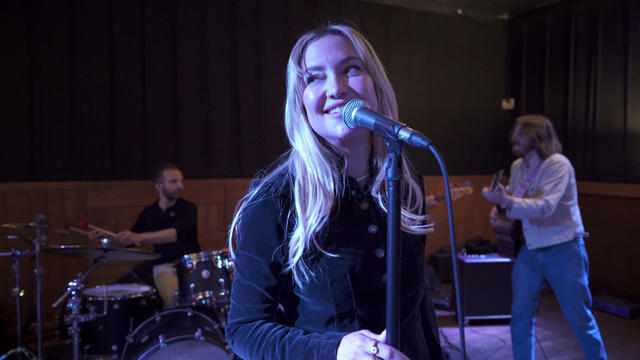
Kate Hudson made a name for herself as an Oscar-nominated actress in "Almost Famous." But music has always been in her blood, and now Hudson is making a name for herself as a singer-songwriter. She talks with correspondent Tracy Smith about her debut album, "Glorious," filled with her songs about life and love, and reveals the one song that truly rips her heart out.

He's been painting for more than 50 years, but artist Stanley Whitney – whose bold, colorful canvases offer vibrant hues and deliberately ferocious brushstrokes – is just now getting his first major retrospective (including many works never before exhibited publicly), at the Buffalo AKG Art Museum in Buffalo, N.Y. Correspondent Alina Cho talks with Whitney about the breakthrough that came during his artistic journey.

Alexis Quaretti is the executive culinary director of Oceania Cruises and oversees more than 30 restaurants across the cruise line's fleet of ships. Michelle Miller has more.

Public baths have been the center of city life in Japan for centuries. But since 2006, hundreds of such baths have closed. Some are working to preserve the ancient tradition, which they say allows for socializing and relaxation.

Multiple people were killed as dozens of tornadoes touched down across the Great Plains over the weekend. Oklahoma was hit particularly hard. Omar Villafranca reports.

Thousands of Israelis again took to the streets this weekend, demanding their government strike a deal to bring home the remaining hostages being held by Hamas. Still, Israel continues to bombard Rafah ahead of an expected ground invasion. Debora Patta reports.

Protests continued on college campuses across the U.S., as students demand their schools divest from Israel and plead for an end to the war in Gaza. More than 100 arrests were made over the weekend. Mark Strassmann reports.

With a little over six months to go until the 2024 election, President Biden and former President Trump are locked in a tight race in several battleground states, according to a new CBS News poll. Skyler Henry breaks down some of the numbers.
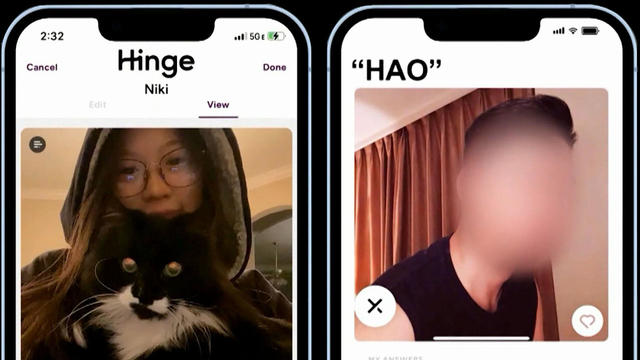
After delving into the world of romance scams, CBS News followed up with several victims whose ordeals were highlighted. Jim Axelrod shares their stories.

A police officer becomes a guardian angel for a little girl struggling at school. A New Jersey toddler goes viral for the way she speaks, bringing joy and laughs to millions. A 7-year-old makes history at the rodeo. Plus, more inspiring stories.

In 1961, Ed Dwight was selected by President John F. Kennedy to enter an Air Force training program known as the path to NASA's Astronaut Corps. But he ultimately never made it to space.

At his lowest moment, U.S. Army veteran and former teacher Billy Keenan found strength in his faith as he was reminded of his own resilience.

A surfing accident left New York teacher Billy Keenan paralyzed, but when he received a call from a police officer, his life changed.

The So Much To Give Inclusive Cafe in Cedars, Pennsylvania employs 63 people — 80% have a disability.

CBS Reports goes to Illinois, which has one of the highest rates of institutionalization in the country, to understand the challenges families face keeping their developmentally disabled loved ones at home.

As more states legalize gambling, online sportsbooks have spent billions courting the next generation of bettors. And now, as mobile apps offer 24/7 access to placing wagers, addiction groups say more young people are seeking help than ever before. CBS Reports explores what experts say is a hidden epidemic lurking behind a sports betting bonanza that's leaving a trail of broken lives.

In February 2023, a quiet community in Ohio was blindsided by disaster when a train derailed and authorities decided to unleash a plume of toxic smoke in an attempt to avoid an explosion. Days later, residents and the media thought the story was over, but in fact it was just beginning. What unfolded in East Palestine is a cautionary tale for every town and city in America.

In the aftermath of the Supreme Court striking down affirmative action in college admissions, CBS Reports examines the fog of uncertainty for students and administrators who say the decision threatens to unravel decades of progress.

CBS Reports examines the legacy of the U.S. government's terrorist watchlist, 20 years after its inception. In the years since 9/11, the database has grown exponentially to target an estimated 2 million people, while those who believe they were wrongfully added are struggling to clear their names.

It's the first meeting between the two men since Florida Governor Ron DeSantis ended his 2024 presidential challenge against former President Trump.

Texans wide receiver Tank Dell "sustained a minor wound" in a shooting that took place early Sunday morning in Florida, the team said.

South Dakota Gov. Kristi Noem addressed on social media the backlash she received after details of her soon-to-be-released book were revealed.

Pope Francis traveled to the lagoon city to visit the Holy See's pavilion at the Biennale contemporary art show and meet with the people who created it.
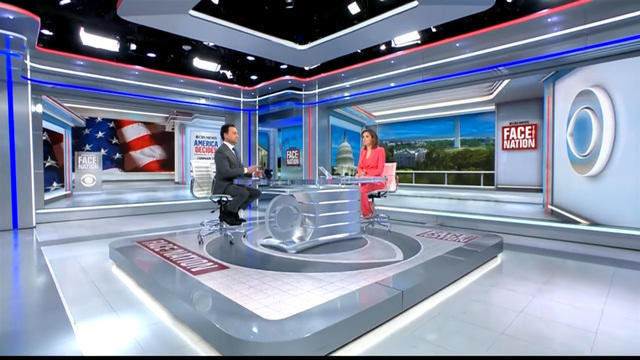
On this "Face the Nation" broadcast, Senate Minority Leader Mitch McConnell and UNICEF executive director Catherine Russell join Margaret Brennan.

The union struck a four-year agreement with the German company on Friday evening, just before the expiration of the previous contract.

Intimacy coordination is a relatively new and growing field with movie and television productions required to make a good-faith effort to hire one if needed on set.

Under the new law signed this week, ByteDance has nine to 12 months to sell the platform to an American owner, or TikTok faces being banned in the U.S.

The income needed to join your state's top earners can vary considerably, from a low of $329,620 annually in West Virginia to $719,253 in Washington D.C.

About 7 in 10 retirees stop working before they turned 65. For many of them, it was for reasons beyond their control.

It's the first meeting between the two men since Florida Governor Ron DeSantis ended his 2024 presidential challenge against former President Trump.

South Dakota Gov. Kristi Noem addressed on social media the backlash she received after details of her soon-to-be-released book were revealed.

Campus protesters are "looking for some sort of acknowledgement from our leadership," Democratic Rep. Summer Lee of Pennsylvania said.

Hanna Siegel's uncle, U.S.-Israeli citizen Keith Siegel, was one of the hostages seen in a Hamas propaganda video Saturday.

On this "Face the Nation" broadcast, Senate Minority Leader Mitch McConnell and UNICEF executive director Catherine Russell join Margaret Brennan.

Around 1 in 5 retail milk samples had tested positive for the bird flu virus, but further tests show it was not infectious.

The White House had been due to decide on the menthol cigarette rule in March.

The discovery of drug-resistant bacteria in two dogs prompted a probe by the CDC and New Jersey health authorities.

First known HIV cases from a nonsterile injection for cosmetic reasons highlights the risk of unlicensed providers.

Are you using your smartwatch to the fullest? Here are 4 metrics doctors say can be useful to track beyond your daily step count.

Pope Francis traveled to the lagoon city to visit the Holy See's pavilion at the Biennale contemporary art show and meet with the people who created it.

The Duke of Sussex will attend the thanksgiving service for the 10th anniversary of the Invictus Games Foundation in London on May 8.

Nonprofit organization World Central Kitchen is set to resume its aid work in Gaza, weeks after seven aid workers were killed.

The hostages seen on the video were identified as Omri Miran and Keith Siegel by the campaign group the Hostages and Missing Families Forum.

Iraqi authorities are investigating the killing of a well-known social media influencer Um Fahad who was shot by an armed motorcyclist in front of her home in central Baghdad.

"Sunday Morning" remembers some of the notable figures who recently left us, including keyboardist Mike Pinder, of The Moody Blues.

She made a name for herself as an Oscar-nominated actress in "Almost Famous." But music has always been in her blood, and now Kate Hudson is making a name for herself as a singer-songwriter, with her debut album, "Glorious."
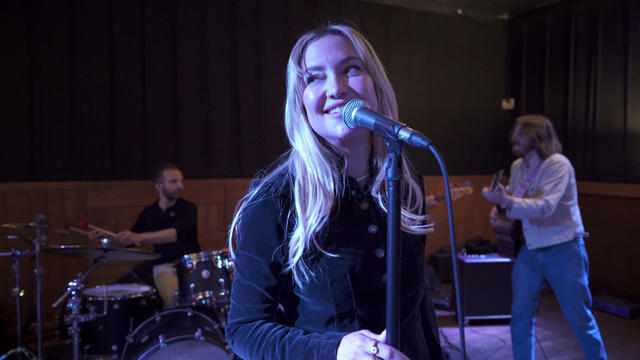
Kate Hudson made a name for herself as an Oscar-nominated actress in "Almost Famous." But music has always been in her blood, and now Hudson is making a name for herself as a singer-songwriter. She talks with correspondent Tracy Smith about her debut album, "Glorious," filled with her songs about life and love, and reveals the one song that truly rips her heart out.

He's been painting for more than 50 years, but artist Stanley Whitney – whose bold, colorful canvases offer vibrant hues and deliberately ferocious brushstrokes – is just now getting his first major retrospective (including many works never before exhibited publicly), at the Buffalo AKG Art Museum in Buffalo, N.Y. Correspondent Alina Cho talks with Whitney about the breakthrough that came during his artistic journey.

This month's fiction and non-fiction titles include the follow-up from Amor Towles, author of the international sensation, "A Gentleman in Moscow."

After delving into the world of romance scams, CBS News followed up with several victims whose ordeals were highlighted. Jim Axelrod shares their stories.

NYU Langone Health and Meta have developed a new type of MRI that dramatically reduces the time needed to complete scans through artificial intelligence. CBS News correspondent Anne-Marie Green reports.

From labor shortages to environmental impacts, farmers are looking to AI to help revolutionize the agriculture industry. One California startup, Farm-ng, is tapping into the power of AI and robotics to perform a wide range of tasks, including seeding, weeding and harvesting.

The Federal Communications Commission voted to adopt net neutrality regulations, a reversal from the policy adopted during former President Donald Trump's administration. Christopher Sprigman, a professor at the New York University School of Law, joins CBS News with more on the vote.

Are you using your smartwatch to the fullest? Here are 4 metrics doctors say can be useful to track beyond your daily step count.

Bats have often been called scary and spooky but experts say they play an important role in our daily lives. CBS News' Danya Bacchus explains why the mammals are so vital to our ecosystem and the threats they're facing.

Pediatrician Dr. Mona Hanna-Attisha, whose work has spurred official action on the Flint water crisis, told CBS News that it's stunning that "we continue to use the bodies of our kids as detectors of environmental contamination." She discusses ways to support victims of the water crisis, the ongoing work of replacing the city's pipes and more in this extended interview.

Ten years ago, a water crisis began when Flint, Michigan, switched to the Flint River for its municipal water supply. The more corrosive water was not treated properly, allowing lead from pipes to leach into many homes. CBS News correspondent Ash-har Quraishi spoke with residents about what the past decade has been like.

According to the University of California, Davis, residential energy use is responsible for 20% of total greenhouse gas emissions in the U.S. However, one company is helping residential buildings reduce their impact and putting carbon to use. CBS News' Bradley Blackburn shows how the process works.

Emerging cicadas are so loud in one South Carolina county that residents are calling the sheriff's office asking why they can hear a "noise in the air that sounds like a siren, or a whine, or a roar." CBS News' John Dickerson has details.

After delving into the world of romance scams, CBS News followed up with several victims whose ordeals were highlighted. Jim Axelrod shares their stories.
After a traditional autopsy, a coroner ruled Kristen Trickle died by suicide. But prosecutors in Kansas questioned if she could have fired the large-caliber revolver that killed her and ordered an autopsy of her mind.

Viktoria Nasyrova attempted to murder a woman with cheesecake. As one private investigator would find out, she had a list of alleged victims — including her ex-boyfriend's dog.

Angel Gabriel Cuz-Choc was found hiding in a wooded area after his girlfriend and her 4-year-old daughter were found dead in Florida.

Dramatic bodycam footage shows the moment Florida deputies and K-9 dogs close in on a double murder suspect hiding in a thickly wooded area.

Astronauts Barry Wilmore and Sunita Williams say they have complete confidence in the Starliner despite questions about Boeing's safety culture.

In 1961, Ed Dwight was selected by President John F. Kennedy to enter an Air Force training program known as the path to NASA's Astronaut Corps. But he ultimately never made it to space.
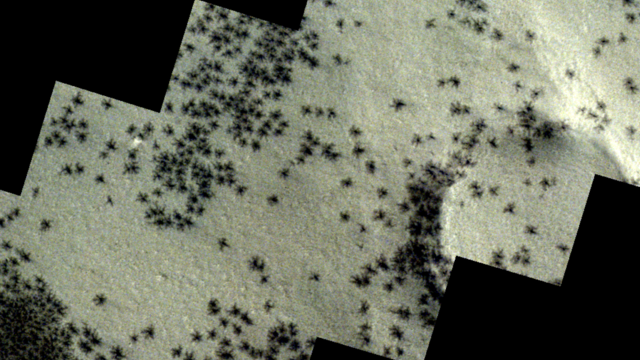
The creepy patterns were observed by the European Space Agency's ExoMars Trace Gas Orbiter.

The Shenzhou 18 crew will replace three taikonauts aboard the Chinese space station who are wrapping up a six-month stay.

In November 2023, NASA's Voyager 1 spacecraft stopped sending "readable science and engineering data."

A look back at the esteemed personalities who've left us this year, who'd touched us with their innovation, creativity and humanity.

The Francis Scott Key Bridge in Baltimore collapsed early Tuesday, March 26 after a column was struck by a container ship that reportedly lost power, sending vehicles and people into the Patapsco River.

When Tiffiney Crawford was found dead inside her van, authorities believed she might have taken her own life. But could she shoot herself twice in the head with her non-dominant hand?

We look back at the life and career of the longtime host of "Sunday Morning," and "one of the most enduring and most endearing" people in broadcasting.

Cayley Mandadi's mother and stepfather go to extreme lengths to prove her death was no accident.

Thousands of gallons of jet fuel contaminated the Navy's drinking water system for Pearl Harbor. Families dealing with health issues are suing, alleging they were harmed by negligence at Red Hill.

After delving into the world of romance scams, CBS News followed up with several victims whose ordeals were highlighted. Jim Axelrod shares their stories.

Cajun Crack'n Seafood in Concord, California, has been using a robot to serve food and clear dishes. The robot, affectionately called Rosie, has become a customer favorite. Itay Hod reports.

Candace Parker, a three-time WNBA champion and two-time Olympic gold medalist, announced Sunday that she is retiring after 16 seasons in the WNBA.

Construction has begun in Las Vegas on what will be the fastest train line in the United States. The line will connect to existing rails in Los Angeles, with the trip between the two destinations expected to take about two hours. Elise Preston has more.